
Physical Penetration Testing/Red Teaming
Sloane Risk Group has built a solid reputation as London’s premiere Physical Penetration Testing company, providing an unequalled service to clients across a range of sectors including finance, insurance, law, facilities, construction, transport and the arts.
Our Penetration Testing service is a critical component of any robust security strategy, providing our clients with a valuable assessment of their security systems, processes and security culture to prevent intrusion and insider threat leading to costly breaches and attacks.
We pride ourselves on the strength and diversity of our expert penetration testing team who have a wide range of skillsets relevant to our unique pen testing service including security assessment, social engineering, lock bypass, infiltration, and security knowledge.
Our experienced consultants explore the threat level and objectives of our clients, presenting them with a bespoke proposal for a test suited to their business, geography, budget, and specific requirements.
Physical Penetration Testing and subsequent staff security awareness training is the first defence against cyber crime.
Also known as Physical Infiltration or Black Teaming
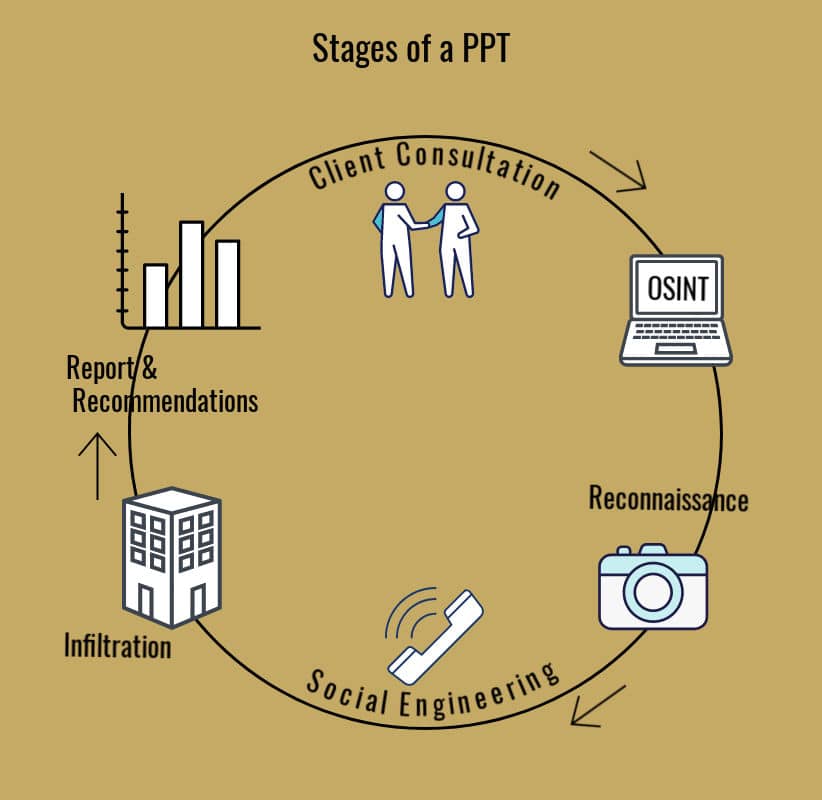
Physical Penetration Testing is a methodology, combining physical intrusion tactics with online research, reconnaissance, social engineering and often a consecutive red team cyber attack.
Physical security is often overlooked as an entry point for malicious actors.
✓ 98% of cyber attacks rely on social engineering.
✓ The average cost of a malware attack on a company is £1.73 million.
✓ Physical Penetration Testing improves staff security awareness of the methods used by social engineers and hostile attackers.
Realistic Intruder Simulation
This real-life approach is proven to detect more vulnerabilities than a box ticking audit style test.
✓ Security vulnerabilities and staff short cuts are easily detected.
✓ Security culture is improved.
✓ Business operations are more secure, reducing risk from competitors and insider threat.
Working carefully within the parameters of agreed tactics and objectives, our experienced Physical Penetration Testing Team will build a picture of your organisation’s security posture with an emphasis on staff security culture.
We will then attempt to gain access to your property and exploitable data regardless of size and existing security measures.
Our professional testers will revisit your premises over a day or a selection of days to conduct the series of tests using testers with a range of profiles suited to your particular business and location.
Following the test, we will create a comprehensive report using a risk assessment matrix to score your security level, carefully considering the risks to your assets versus real world threats. We will then make recommendations of how you can improve your current residential or corporate security.
A popular option, often requested by our clients, is to use our findings to create and deliver bespoke staff training packages to increase the awareness of your staff and improve the security culture of your business. This is carefully delivered in a friendly and constructive manner, emphasising to staff and stakeholders why it is vital that security procedures are followed.
We also offer a Digital Profiling service for executives, this will identify online vulnerabilities which we can then remove where possible. Each client is given a strategy to implement which will improve their privacy leading to better business and personal security.
Benefits of a Physical Penetration Test
✓ Physical Penetration Testing adds weight to requests for security budget increases.
✓ Impartial advice detects unknown security vulnerabilities
✓ Comprehensive reporting and a clearly outlined strategy for improvement
✓ Competitive pricing and a highly professional service
Case Study
Physical Penetration Testing
Our client was a CSO who had just commenced a new role within a global law firm with offices in London and four other UK cities. His requirement was to quickly establish the security posture of the buildings, the staff security culture, and to identify any vulnerabilities which required attention.
Our first step was to conduct a thorough client consultation. We established the locations that we would be testing, the known and potential unknown adversaries faced by the business, and the client’s appetite for our range of tests. This was a chance for us to explain our capabilities to the client and to gain an understanding of who the threat actors were, enabling us to create a range of tests to realistically replicate the measures that they would use.
The law firm's primary concerns were the threats of well planned attacks from criminal entities with the aim of obtaining their clients personal information and that relating to ongoing cases, and the threat from opportunistic attackers who may seek to gain entry in order to steal hardware or other office items.
Once we had agreed the scope of our tests, we conducted reconnaissance of each building to be tested, this lasted for five days in each location, during which time we identified who the contractors, suppliers, staff and visitors were, what time various contractors arrived, how the security measures operated and the obvious physical weaknesses of the buildings.
We then spent two weeks researching the business as a whole, the individual offices, the key executives and employees. The information that we gained assisted us in deploying social engineering methods to identify additional information regarding the workings of the business and we started to draw up a plan of how we would gain access to the buildings.
We chose our team based on the pretexts that we thought would enable us to gain entry, they ranged from facilities and contractor guises to visiting executives from other offices.
Our test week was planned as simultaneous attacks to prevent any suspicious interest being conveyed between sites. Within the course of the week, we gained entry to every building, some multiple times.
Our aim is rarely to just gain entry. When replicating an attack, we need to reach the targets that the adversaries would aim for. One inside we wanted to prove that confidential information could be accessed, items could be removed, and we could exit without detection. We are also continuously assessing as we move through the building, we need to present our clients with highly comprehensive reports which make genuine recommendations to enhance their security and safety.
A big part of our testing is around the security of the organisations people, very often people can be coerced or tricked into providing information and providing access. Our aim is to present these findings neutrally without blame, in a way which people will learn and adopt different security techniques.
In this instance, our physical infiltrations resulted in accessing unlocked computers, gaining information relating to the WIFI used, inserting keylogging devices onto computers, installing replica audio eavesdropping and video bugging devices, and the removal of hard drives. We found passwords, personal information and an access badge that allowed our entry into the most secure parts of the buildings.
We were not compromised at any of the buildings and the hardware that we removed was not reported as missing until we were a considerable distance from the target buildings.
Our report was presented to the client, who was able to request a budget to improve some access control measures, and most importantly develop a staff training package to ensure that vital policy and procedure information was communicated correctly to staff and the correct control measures were adopted.
The financial cost of our project was minimal compared to the damage that could have been caused by a genuine hostile attacker.




